在Windows系统中创建了一个带区动态卷,其实就是用两个磁盘以RAID0方式整合也一个大磁盘。但启动进入Ubuntu (14.04) 系统后并不能正确识别。下图是我在测试系统中创建了一个带区卷E:(由2个盘构成)和一个RAID5卷F:(由4个盘构成):
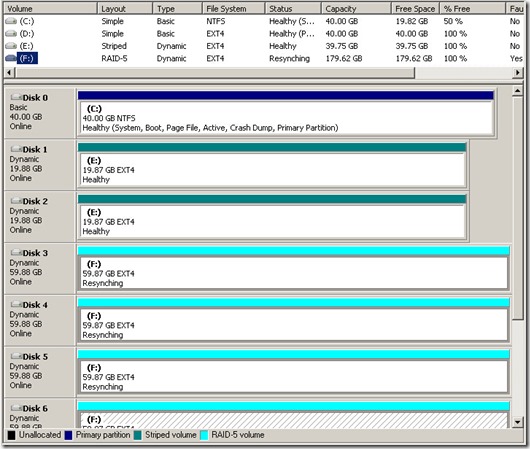
这两个由Windows系统创建的动态卷,是LDM格式(Logical Disk Manager),Linux系统中不能正确识别。最初我尝试用mdadm强制加载带区卷,分别试了64K及128K chunk,但全部无效,尝试办法如下:
root@ubuntu:~# mdadm --build /dev/md0 --level=0 --chunk=128 --raid-devices=2 /dev/sd[cd]3
mdadm: array /dev/md0 built and started.
root@ubuntu:~# mdadm --detail /dev/md0
/dev/md0:
Version :
Creation Time : Thu Jun 25 16:08:11 2015
Raid Level : raid0
Array Size : 41680640 (39.75 GiB 42.68 GB)
Raid Devices : 2
Total Devices : 2
State : clean
Active Devices : 2
Working Devices : 2
Failed Devices : 0
Spare Devices : 0
Chunk Size : 128K
Number Major Minor RaidDevice State
0 8 35 0 active sync /dev/sdc3
1 8 51 1 active sync /dev/sdd3
root@ubuntu:~# tune2fs -l /dev/md0
tune2fs 1.42.9 (4-Feb-2014)
tune2fs: Bad magic number in super-block while trying to open /dev/md0
Couldn't find valid filesystem superblock.
root@ubuntu:~# mdadm -S /dev/md0
mdadm: stopped /dev/md0
root@ubuntu:~# mdadm --build /dev/md0 --level=0 --chunk=128 --raid-devices=2 /dev/sd[dc]3
mdadm: array /dev/md0 built and started.
root@ubuntu:~# mdadm --detail /dev/md0
/dev/md0:
Version :
Creation Time : Thu Jun 25 16:08:57 2015
Raid Level : raid0
Array Size : 41680640 (39.75 GiB 42.68 GB)
Raid Devices : 2
Total Devices : 2
State : clean
Active Devices : 2
Working Devices : 2
Failed Devices : 0
Spare Devices : 0
Chunk Size : 128K
Number Major Minor RaidDevice State
0 8 51 0 active sync /dev/sdd3
1 8 35 1 active sync /dev/sdc3
root@ubuntu:~# tune2fs -l /dev/md0
tune2fs 1.42.9 (4-Feb-2014)
tune2fs: Bad magic number in super-block while trying to open /dev/md0
Couldn't find valid filesystem superblock.
root@ubuntu:~# mdadm -S /dev/md0
mdadm: stopped /dev/md0
root@ubuntu:~#
后来几经搜索,发现解决方案原来很简单,只需要安装ldmtool。
root@ubuntu:~# parted -l
Model: VMware, VMware Virtual S (scsi)
Disk /dev/sda: 85.9GB
Sector size (logical/physical): 512B/512B
Partition Table: msdos
Number Start End Size Type File system Flags
1 1049kB 1000MB 999MB primary ext2 boot
2 1000MB 81.0GB 80.0GB primary xfs
3 81.0GB 85.9GB 4898MB primary linux-swap(v1)
Model: VMware, VMware Virtual S (scsi)
Disk /dev/sdb: 42.9GB
Sector size (logical/physical): 512B/512B
Partition Table: msdos
Number Start End Size Type File system Flags
1 1049kB 42.9GB 42.9GB primary ext4
Model: VMware, VMware Virtual S (scsi)
Disk /dev/sdc: 21.5GB
Sector size (logical/physical): 512B/512B
Partition Table: gpt
Number Start End Size File system Name Flags
1 17.4kB 1066kB 1049kB LDM metadata partition
2 1066kB 134MB 133MB Microsoft reserved partition msftres
3 134MB 21.5GB 21.3GB LDM data partition
Model: VMware, VMware Virtual S (scsi)
Disk /dev/sdd: 21.5GB
Sector size (logical/physical): 512B/512B
Partition Table: gpt
Number Start End Size File system Name Flags
1 17.4kB 1066kB 1049kB LDM metadata partition
2 1066kB 134MB 133MB Microsoft reserved partition msftres
3 134MB 21.5GB 21.3GB LDM data partition
Model: VMware, VMware Virtual S (scsi)
Disk /dev/sde: 64.4GB
Sector size (logical/physical): 512B/512B
Partition Table: gpt
Number Start End Size File system Name Flags
1 17.4kB 1066kB 1049kB LDM metadata partition
2 1066kB 134MB 133MB Microsoft reserved partition msftres
3 134MB 64.4GB 64.3GB LDM data partition
Model: VMware, VMware Virtual S (scsi)
Disk /dev/sdf: 64.4GB
Sector size (logical/physical): 512B/512B
Partition Table: gpt
Number Start End Size File system Name Flags
1 17.4kB 1066kB 1049kB LDM metadata partition
2 1066kB 134MB 133MB Microsoft reserved partition msftres
3 134MB 64.4GB 64.3GB LDM data partition
Model: VMware, VMware Virtual S (scsi)
Disk /dev/sdg: 64.4GB
Sector size (logical/physical): 512B/512B
Partition Table: gpt
Number Start End Size File system Name Flags
1 17.4kB 1066kB 1049kB LDM metadata partition
2 1066kB 134MB 133MB Microsoft reserved partition msftres
3 134MB 64.4GB 64.3GB LDM data partition
Model: VMware, VMware Virtual S (scsi)
Disk /dev/sdh: 64.4GB
Sector size (logical/physical): 512B/512B
Partition Table: gpt
Number Start End Size File system Name Flags
1 17.4kB 1066kB 1049kB LDM metadata partition
2 1066kB 134MB 133MB Microsoft reserved partition msftres
3 134MB 64.4GB 64.3GB LDM data partition
root@ubuntu:~# ldmtool scan
[
"3ffea520-1b24-11e5-8565-000c293dbd64"
]
root@ubuntu:~# ldmtool show diskgroup 3ffea520-1b24-11e5-8565-000c293dbd64
{
"name" : "WIN-FB20IXK90MU-Dg0",
"guid" : "3ffea520-1b24-11e5-8565-000c293dbd64",
"volumes" : [
"Volume2",
"Volume1"
],
"disks" : [
"Disk1",
"Disk2",
"Disk3",
"Disk4",
"Disk6",
"Disk5"
]
}
root@ubuntu:~# ldmtool show volume 3ffea520-1b24-11e5-8565-000c293dbd64 Volume1
{
"name" : "Volume1",
"type" : "RAID5",
"size" : 376688640,
"chunk-size" : 128,
"hint" : "F:",
"partitions" : [
"Disk1-01",
"Disk2-01",
"Disk3-01",
"Disk4-01"
]
}
root@ubuntu:~# ldmtool show volume 3ffea520-1b24-11e5-8565-000c293dbd64 Volume2
{
"name" : "Volume2",
"type" : "striped",
"size" : 83353600,
"chunk-size" : 128,
"hint" : "E:",
"partitions" : [
"Disk5-01",
"Disk6-01"
]
}
root@ubuntu:~# ldmtool show partition 3ffea520-1b24-11e5-8565-000c293dbd64 Disk1-01
{
"name" : "Disk1-01",
"start" : 2014,
"size" : 125562880,
"disk" : "Disk1"
}
root@ubuntu:~# ldmtool show partition 3ffea520-1b24-11e5-8565-000c293dbd64 Disk2-01
{
"name" : "Disk2-01",
"start" : 2014,
"size" : 125562880,
"disk" : "Disk2"
}
root@ubuntu:~# ldmtool show partition 3ffea520-1b24-11e5-8565-000c293dbd64 Disk3-01
{
"name" : "Disk3-01",
"start" : 2014,
"size" : 125562880,
"disk" : "Disk3"
}
root@ubuntu:~# ldmtool show partition 3ffea520-1b24-11e5-8565-000c293dbd64 Disk4-01
{
"name" : "Disk4-01",
"start" : 2014,
"size" : 125562880,
"disk" : "Disk4"
}
root@ubuntu:~# ldmtool show partition 3ffea520-1b24-11e5-8565-000c293dbd64 Disk5-01
{
"name" : "Disk5-01",
"start" : 2014,
"size" : 41676800,
"disk" : "Disk5"
}
root@ubuntu:~# ldmtool show partition 3ffea520-1b24-11e5-8565-000c293dbd64 Disk6-01
{
"name" : "Disk6-01",
"start" : 2014,
"size" : 41676800,
"disk" : "Disk6"
}
用ldmtool解析并创建动态卷只需要一个简单命令:
root@ubuntu:~# ldmtool create all
[
"ldm_vol_WIN-FB20IXK90MU-Dg0_Volume2",
"ldm_vol_WIN-FB20IXK90MU-Dg0_Volume1"
]
root@ubuntu:~# ls -l /dev/mapper/
total 0
crw------- 1 root root 10, 236 Jun 25 16:29 control
lrwxrwxrwx 1 root root 7 Jun 25 16:29 ldm_part_WIN-FB20IXK90MU-Dg0_Disk1-01 -> ../dm-1
lrwxrwxrwx 1 root root 7 Jun 25 16:29 ldm_part_WIN-FB20IXK90MU-Dg0_Disk2-01 -> ../dm-2
lrwxrwxrwx 1 root root 7 Jun 25 16:29 ldm_part_WIN-FB20IXK90MU-Dg0_Disk3-01 -> ../dm-3
lrwxrwxrwx 1 root root 7 Jun 25 16:29 ldm_part_WIN-FB20IXK90MU-Dg0_Disk4-01 -> ../dm-4
lrwxrwxrwx 1 root root 7 Jun 25 16:29 ldm_vol_WIN-FB20IXK90MU-Dg0_Volume1 -> ../dm-5
lrwxrwxrwx 1 root root 7 Jun 25 16:29 ldm_vol_WIN-FB20IXK90MU-Dg0_Volume2 -> ../dm-0
root@ubuntu:~# ls -l /dev/dm*
brw-rw---- 1 root disk 252, 0 Jun 25 16:29 /dev/dm-0
brw-rw---- 1 root disk 252, 1 Jun 25 16:29 /dev/dm-1
brw-rw---- 1 root disk 252, 2 Jun 25 16:29 /dev/dm-2
brw-rw---- 1 root disk 252, 3 Jun 25 16:29 /dev/dm-3
brw-rw---- 1 root disk 252, 4 Jun 25 16:29 /dev/dm-4
brw-rw---- 1 root disk 252, 5 Jun 25 16:29 /dev/dm-5
root@ubuntu:~#
root@ubuntu:~# tune2fs -l /dev/dm-0
tune2fs 1.42.9 (4-Feb-2014)
Filesystem volume name: <none>
Last mounted on: <not available>
Filesystem UUID: 22a45231-ede2-4c60-9c93-ee841ae2f2ee
Filesystem magic number: 0xEF53
Filesystem revision #: 1 (dynamic)
Filesystem features: has_journal ext_attr resize_inode dir_index filetype extent flex
_bg sparse_super large_file huge_file uninit_bg dir_nlink extra_isize
Filesystem flags: signed_directory_hash
Default mount options: user_xattr acl
Filesystem state: clean
Errors behavior: Continue
Filesystem OS type: Linux
Inode count: 2605056
Block count: 10419200
Reserved block count: 520960
Free blocks: 10210674
Free inodes: 2605045
First block: 0
Block size: 4096
Fragment size: 4096
Reserved GDT blocks: 1021
Blocks per group: 32768
Fragments per group: 32768
Inodes per group: 8192
Inode blocks per group: 512
RAID stride: 16
RAID stripe width: 32
Flex block group size: 16
Filesystem created: Thu Jun 25 15:58:29 2015
Last mount time: n/a
Last write time: Thu Jun 25 15:58:31 2015
Mount count: 0
Maximum mount count: -1
Last checked: Thu Jun 25 15:58:29 2015
Check interval: 0 (<none>)
Lifetime writes: 132 MB
Reserved blocks uid: 0 (user root)
Reserved blocks gid: 0 (group root)
First inode: 11
Inode size: 256
Required extra isize: 28
Desired extra isize: 28
Journal inode: 8
Default directory hash: half_md4
Directory Hash Seed: a472f2f6-a27b-4362-91e2-dce4ad48a700
Journal backup: inode blocks
root@ubuntu:~# tune2fs -l /dev/dm-5
tune2fs 1.42.9 (4-Feb-2014)
Filesystem volume name: <none>
Last mounted on: <not available>
Filesystem UUID: f0655359-b2e0-4732-8df0-b0ab24918ec1
Filesystem magic number: 0xEF53
Filesystem revision #: 1 (dynamic)
Filesystem features: has_journal ext_attr resize_inode dir_index filetype extent flex
_bg sparse_super large_file huge_file uninit_bg dir_nlink extra_isize
Filesystem flags: signed_directory_hash
Default mount options: user_xattr acl
Filesystem state: clean
Errors behavior: Continue
Filesystem OS type: Linux
Inode count: 11771904
Block count: 47086080
Reserved block count: 2354304
Free blocks: 46299313
Free inodes: 11771893
First block: 0
Block size: 4096
Fragment size: 4096
Reserved GDT blocks: 1012
Blocks per group: 32768
Fragments per group: 32768
Inodes per group: 8192
Inode blocks per group: 512
RAID stride: 16
RAID stripe width: 48
Flex block group size: 16
Filesystem created: Thu Jun 25 15:13:55 2015
Last mount time: n/a
Last write time: Thu Jun 25 15:14:21 2015
Mount count: 6
Maximum mount count: -1
Last checked: Thu Jun 25 15:14:21 2015
Check interval: 0 (<none>)
Lifetime writes: 133 MB
Reserved blocks uid: 0 (user root)
Reserved blocks gid: 0 (group root)
First inode: 11
Inode size: 256
Required extra isize: 28
Desired extra isize: 28
Journal inode: 8
Default directory hash: half_md4
Directory Hash Seed: 88ddd8a2-506a-4e9b-9109-ce9c171b2607
Journal backup: inode blocks
至此就可以自由访问 /dev/dm-0和/dev/dm-5两个设备卷了。不过还要说的是,ldmtool是通过DM (Device Mapper) 产生的RAID卷(和LVM使用的是同样的机制),而不是最常用的MD方式(即Multiple Devices),特别对于RAID5/RAID6此类的数据卷,MD Raid做了较多的优化,除性能更好之外,稳定性应该也好于Device Mapper方式。
参考阅读:
1,http://manpages.ubuntu.com/manpages/trusty/man1/ldmtool.1.html
2,https://github.com/mdbooth/libldm
3,https://notesbytom.wordpress.com/2012/06/14/linux-support-for-windows-dynamic-disks/
4,http://stackoverflow.com/questions/8427372/windows-spanned-disks-ldm-restoration-with-linux/22108676#22108676 <ldmtool出现之前的办法  >
>